Hackers will trawl the internet using specially designed scripts, looking for vulnerabilities in a VoIP users firewall – like an open port. Once a weakness is detected, the hackers will try and authenticate their access and gain control of a PBX system. This is particularly easy if the system operator is still using the default password, or using a generic password that’s easy to crack. Once the password has been cracked, they will have control over the traffic that passes through the PBX system.
Once your PBX is in control of an overseas computer hacker, they need to turn that control into revenue before the network operator realises something is awry. The usual method is to direct your traffic to a premium-rate phone number, where you’re charged per-minute above the cost of the call connection – like an adult chat number or a psychic hotline. And at the time you notice this, your invoice will be sky high.
The amount and variety of cyber threats is constantly increasing. Although awareness among potential victims is on the rise, attackers continue to develop more sophisticated threats and the drivers to hack become more dominant as the potential gain from a successful cyberattack keeps growing. Hackers also constantly improve their ability to lure, which is crucial for their success.
Axeos does not manage your pbx. You and your supplier or administrator are responsible for a sound security of your pbx. Your administrator should do the utmost to prevent pbx misuse.
Hacking can also start from within your own network, for instance from an infected pc. In that case your firewall cannot do much to prevent this.
Axeos PBX offers options to lower the risks drastically. We have written step-by-step instructions you can carry out, so you will be able to use your pbx safely.
Setting up all security measures can be quite complex. Especially setting up the firewall is a precise job and should be executed by someone with the right knowledge. If you do not have that knowledge in your office, please make sure you hire someone to set this up or check your settings.
Step-by-step instructions
A word of advice: please run through áll steps. The single measures offer inadequate security. Even if you follow all steps completely, unfortunately this will not guarantee 100% security. Cyber criminals are creative and know these measures as well. Also, if you have an infected pc or a leak in your company’s network, these stept will not help.
For the latest settings and security-updates of your pbx, you can of course contact your pbx-supplier.
Step 1: Passwords
Use long and strong passwords. Use different passwords for different vpbx-es and for different accounts.
Use the option in the Axeos pbx to generate strong passwords for you.
You need passwords in the following parts of the pbx:
– phones: Communication/Phones
– users: System/Users
You cannot change the password of your SIP trunk yourself: if you think this password is not strong, please ask your provider to change it.
Step 2: Use the Abuse Prevention function
Enable ‘Abuse Prevention’ in menu System/Abuse Prevention. Make sure the IP Adress of your office is set in the ‘Do-not-block’-section.
Step 3: IP Sets and Firewall
Only trust known IP-addresses in the firewall and block all unknown IP-addresses by default (especially SIP-traffic, port 5060-5069).
For allowing audio: open audio (=RTP or media) for 0.0.0.0/0 udp 10000:40000 (these are ports without service).
Do not open port 443 (HTTPS) for the world and force HTTPS (see step 6).
If you really want or need to open up the firewall further, be aware of the risks and IN ANY CASE follow the measures in step 6.
As of version 4.1.10 the vpbx offers the possibility to get a DENY on a blacklist (voipbl) with the use of IP Sets.
You can also create your own IP Sets.
The use of mobile phones
Two scenarios with the use of a mobile phone are:1. The use of a browser to operate the pbx-web interface;2. Use of the smartphone to make calls with the Axeos Phone (or other soft phone).You can use IP Sets to adjust the firewall at these scenarios.- At scenario 1, if you do not use your mobile phone to call with a soft phone, it suffices to open HTTPS (port 443) for the data network of your 4G provider. We have an IP Set with the IP addresses of all known 4G providers.
- At scenario 2: if you do use Axeos Phone to make voip calls on your smartphone, you need to add VoIP (udp+tcp port 5060 and 5061) and media (udp 10000-40000) in addition to HTTPS. Should you not want the ability to use the webinterface on your smartphone but you do want to be able to make calls, you can limit GUI access to only your office’s IP-address in System/Network Servers. With this, Axeos Phone is fully functional without GUI-access to the pbx.
Make sure to make every firewall-rule as specific as possible by choosing for a certain service to allow. Do not think light about choosing ‘all services’ in a firewall rule: your firewall will be dangerously open!
Step 4: Updates
Always install the latest updates. When you get the message there is a new update, ask your provider to install it for you.
Step 5: Logs and reports
Make sure you get good reports with the internal phone log. With reliable reports you will be able to recognize fraudulent use at an early stage. There are several ways to see logs:
– in menu Status/Log viewer.
– the email-address you fill in at System/Options/Mail and SMTP will be used to send CDR information and system messages to. This way you will be informed of changes.
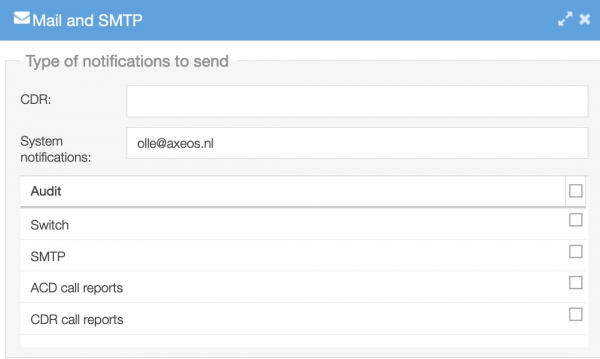
– You can also send logs to an external server. You can set this in System/Options/Logging.
And last but not least, you can use our extensive reporting tool. If you are interested, please contact your supplier or us: sales@axeos.com.
Step 6: Settings Network Servers
In System/Options/Network Servers you can further limit access to certain functions by setting IP-subnets you want to allow. These are comma-seperated lists to make it possible to set multiple subnets or hosts. Enable the switches.

Step 7: Permissions
Hackers often misuse pbx-es to make calls to expensive phone numbers somewhere in the world, in order to earn lots of money. You can limit the damage if you do not allow your users to call to certain countries. Think about almost all countries in Africa and Asia (except for Japan).
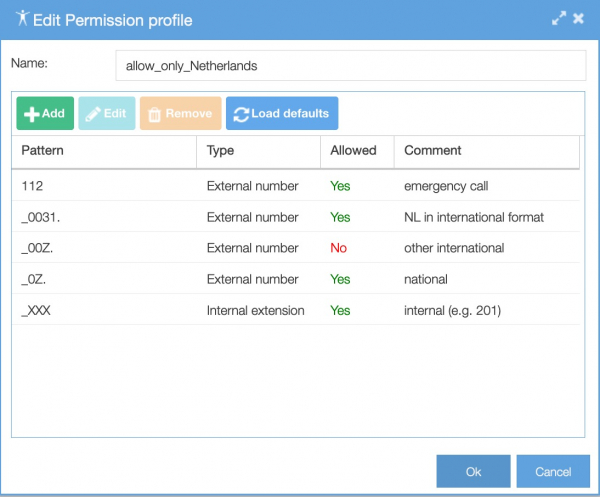
Take in consideration which users do not need to make international phone calls and give all users a permission profile that is as limited as possible. You do this in menu Services/Permission profiles. In this example only telephone numbers in the Netherlands are allowed:
Step 8: Trunks
Make sure the day/week limit on your SIP trunk fits your use: if there would be unauthorized use of your pbx, this limit makes sure that the calls will be stopped much faster. This way your call costs will not rise explosively.
Look at your average calling behaviour and ask your providor to adjust the limit to this.