IDS, Intrusion Detection Syste, is our abuse prevention system that is a very powerful security function. If the service is enabled, the server will respond to suspicious traffic by limiting and/or blocking it automatically. We strongly advise to use this function, along with a correctly configured firewall, as it improves the security level of the platform.
Abuse Prevention is not a replacement for your Firewall and strong passwords. You should secure your PBX with all possible functionality the PBX offers. For more information on how to secure your PBX from hackers, please read this article in our knowledge-base.
Caveat: We advise you to monitor ‘Event log’ and ‘Current blockades’ tabs in Status → Abuse prevention Status. Proper monitoring of the Abuse prevention activity will make troubleshooting easier and will help you to avoid technical problems on valid phones: incorrectly tuned parameters can cause problems, e.g. few phones using the same IP address can be treated as suspicious traffic. In this case the IP address should be added in the “Do not block” box.
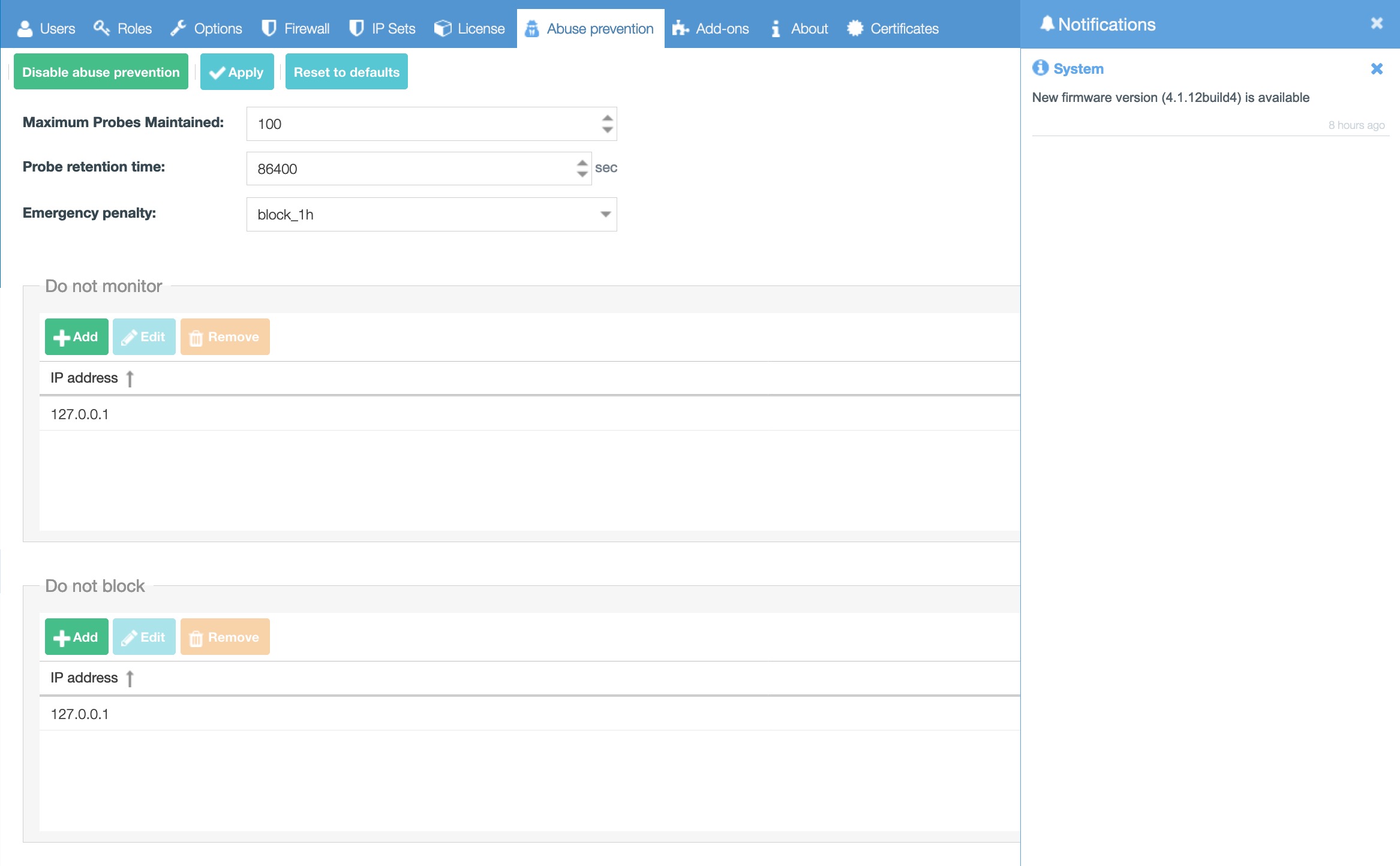
Probe settings
-
Maximum Probes Maintained: how many probes to keep. Minimum value is 100.
-
Probe retention time: how long to keep a host probe after the last matching event.
-
Emergency penalty: penalty which will be applied when “Maximum probes” limit is exceeded.
Do not monitor
List of IPv4 or IPv6 IP addresses which will not be monitored.
Do not block
List of IPv4 or IPv6 IP addresses which will not be bocked when monitoring results would match to suspicious traffic.
Useful when few phones are using the same IP address. In this case the phone IP address should be added here.
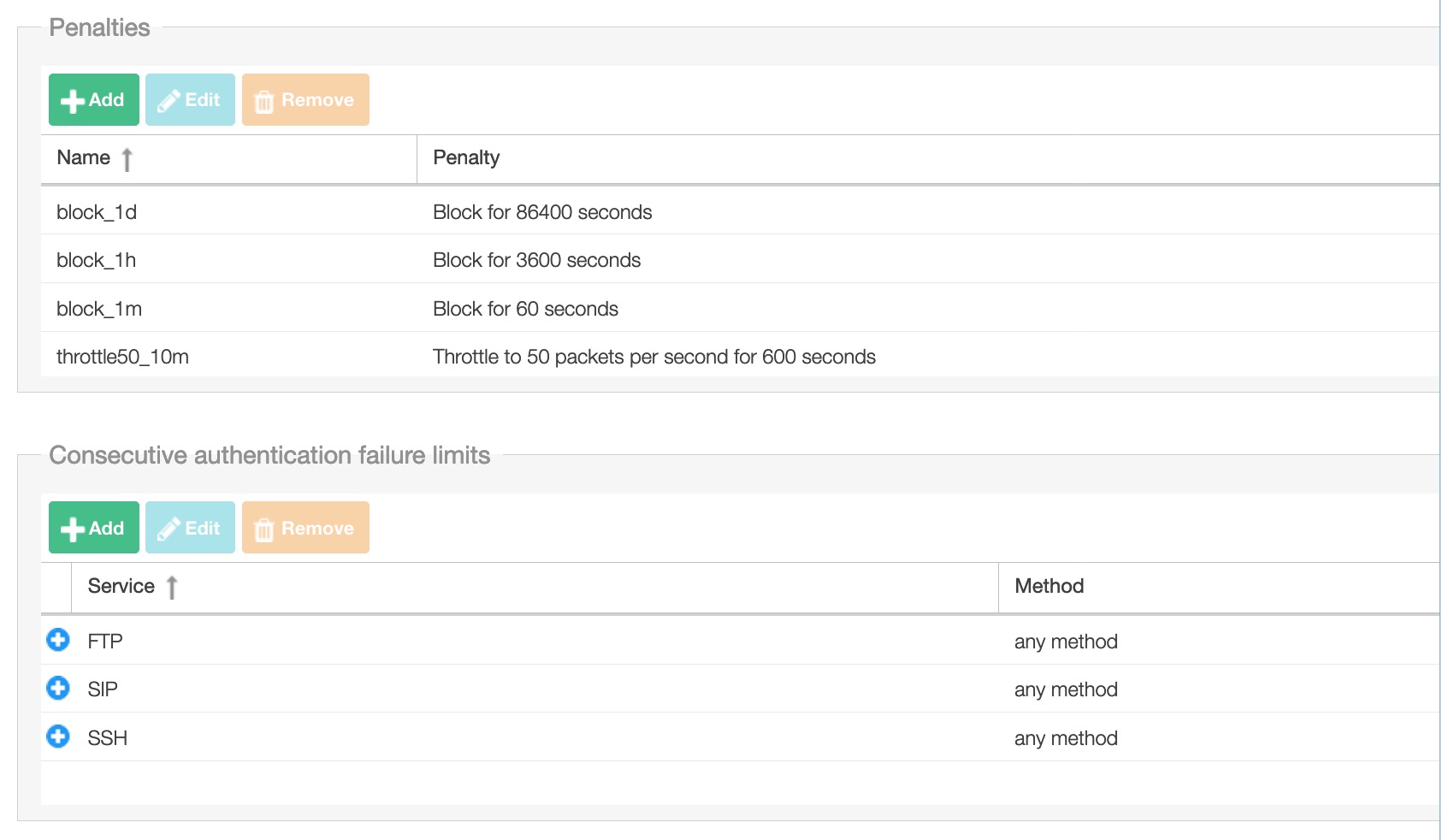
Penalties
This is an editable penalties list where you can also add your own.
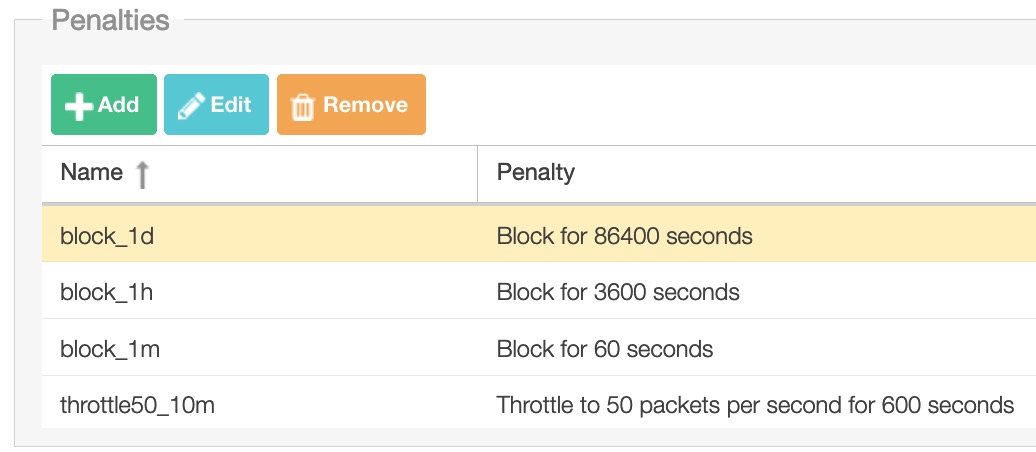
Default penalties:
-
block_1d – block IP address for one day
-
block_1h – block IP address for one hour
-
block_1m – block IP address for one minute
-
throttle5 – limit traffic to 5 packets per second for 60 seconds
-
throttle50 – limit traffic to 50 packets per second for 60 seconds
Consecutive authentication failure limits
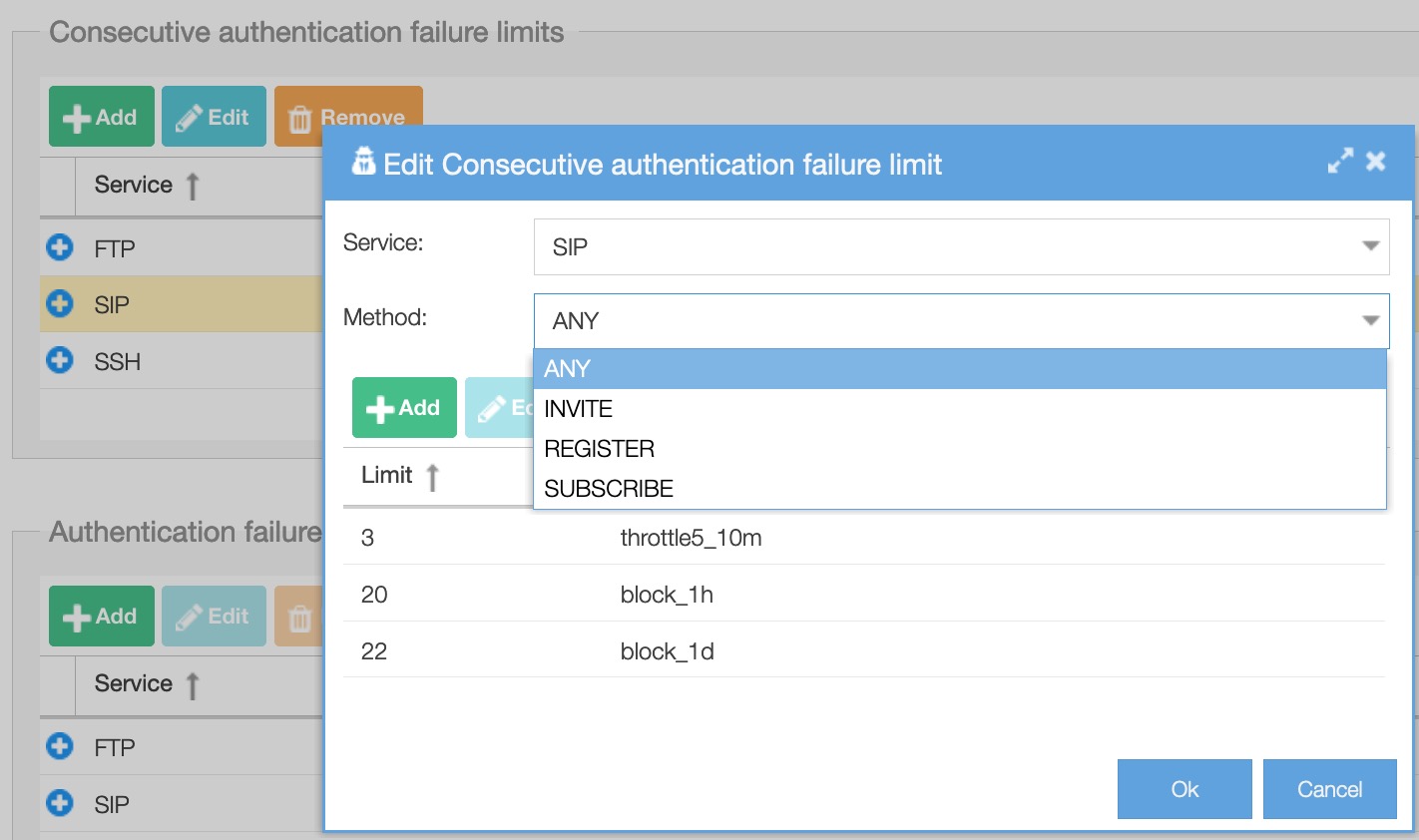
List of limits for consecutive authentication failure
-
Service: SIP or SSH
-
Method: ‘INVITE’, ‘REGISTER’, ‘SUBSCRIBE’. Default ‘any’
-
Limit: The minimum value for this field is 3
-
Penalty: selectable from the ‘Penalties’ list
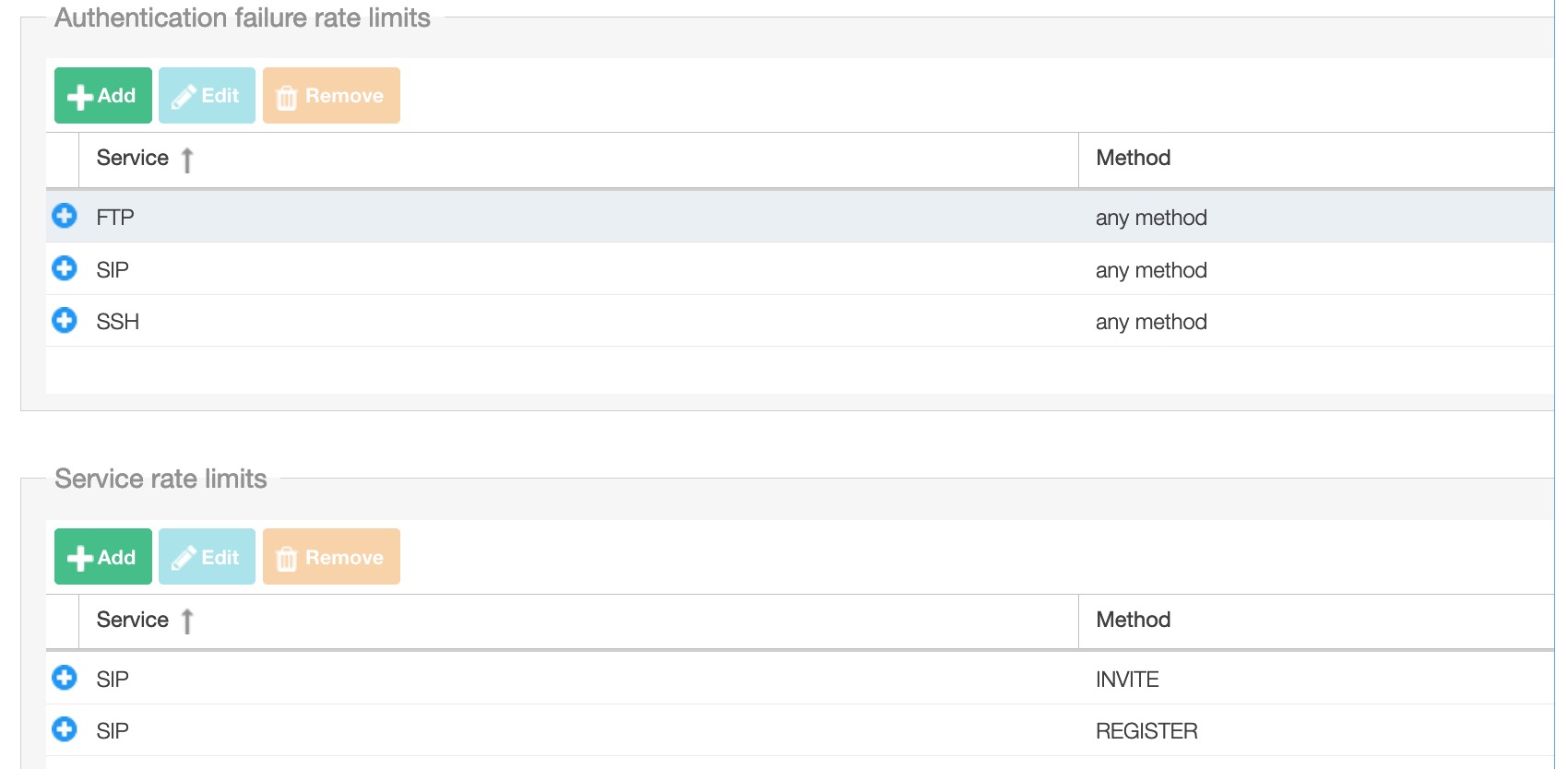
Authentication failure rate limits
List of limits for authentication failure
-
Service: SIP or SSH
-
Method: ‘INVITE’, ‘REGISTER’, ‘SUBSCRIBE’. Default ‘any’
-
Rate failures / second (minute or hour):
-
Burst: Default ’10’
-
Penalty: selectable from the ‘Penalties’ list
Service rate limits
List of limits for a general (successful or not) service rate
-
Service: SIP or SSH
-
Method: ‘INVITE’, ‘REGISTER’, ‘SUBSCRIBE’. Default ‘any’
New limit rule:
-
Rate events / second, (minute or hour):
-
Burst: Default ’10’
-
Penalty: selectable from the ‘Penalties’ list
I blocked myself. What should I do?
If you accidentally block your own devices, you can restart the IDS by clicking “disable abuse prevention” and then enabling it again. Be aware that this will clear probes and blockades that were previously active.